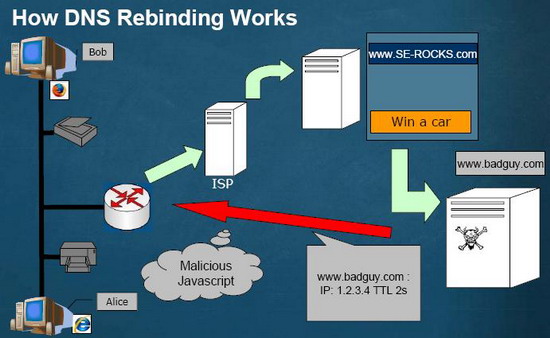
The attacker registers a domain which is delegated to a DNS server he controls. The server is configured to respond with a very short TTL parameter, which prevents the response from being cached....

The first response contains the IP address of the server hosting the malicious code. Subsequent responses contain spoofed private network IP addresses (RFC1918), presumably behind a firewall, being target of the attacker.
Because both are fully valid DNS responses, they authorize the sandboxed script to access hosts inside the private network. By returning multiple short-lived IP addresses, the DNS server enables the script to scan the local network or perform other malicious activities.